Hi,
I am working on the ble_app_template project.
1-How can I enable simple pairing without NFC?
2-Also how can I set pairing code?
3-Is the write way to secure characteristics?
attr_md.rd_auth = 1;
attr_md.wr_auth = 1;
Thanks!
Hi,
I am working on the ble_app_template project.
1-How can I enable simple pairing without NFC?
2-Also how can I set pairing code?
3-Is the write way to secure characteristics?
attr_md.rd_auth = 1;
attr_md.wr_auth = 1;
Thanks!
Hi Muqarrab,
Please see the Security parameters documentation for pairing and this post for secure characteristics.
-Amanda H.
Thanks, Amanda Hsieh
Can we perform Just Works bonding(without entering any key) without NFC Antenna?
Hi, Amanda Hsieh,
As per your instruction, I have added BLE_GAP_CONN_SEC_MODE_SET_ENC_NO_MITM().
Now when I read/write characteristics device starts bonding.
Now can you please confirm that without pairing anyone can't read/write characteristics?
Hi,
Muqarrab said:can you please confirm that without pairing anyone can't read/write characteristics?
if you use BLE_GAP_CONN_SEC_MODE_SET_ENC_NO_MITM() a peer that pairs with Just Works will be able to access the characteristic value.
Please see the documentation:
BLE_GAP_CONN_SEC_MODE_SET_ENC_NO_MITM
Set sec_mode pointed to by ptr to require encryption, but no MITM protection.
-Amanda H.
Hi,
Are you talking about this?
/**@brief GAP connection security modes.
*
* Security Mode 0 Level 0: No access permissions at all (this level is not defined by the Bluetooth Core specification).\n
* Security Mode 1 Level 1: No security is needed (aka open link).\n
* Security Mode 1 Level 2: Encrypted link required, MITM protection not necessary.\n
* Security Mode 1 Level 3: MITM protected encrypted link required.\n
* Security Mode 1 Level 4: LESC MITM protected encrypted link using a 128-bit strength encryption key required.\n
* Security Mode 2 Level 1: Signing or encryption required, MITM protection not necessary.\n
* Security Mode 2 Level 2: MITM protected signing required, unless link is MITM protected encrypted.\n
*/
typedef struct
{
uint8_t sm : 4; /**< Security Mode (1 or 2), 0 for no permissions at all. */
uint8_t lv : 4; /**< Level (1, 2, 3 or 4), 0 for no permissions at all. */
} ble_gap_conn_sec_mode_t;
uint32_t custom_value_char_add(ble_cus_t * p_cus, const ble_cus_init_t * p_cus_init)
{
uint32_t err_code;
ble_gatts_char_md_t char_md;
ble_gatts_attr_md_t cccd_md;
ble_gatts_attr_t attr_char_value;
ble_uuid_t ble_uuid;
ble_gatts_attr_md_t attr_md;
memset(&char_md, 0, sizeof(char_md));
char_md.char_props.read = 1;
char_md.char_props.write = 1;
char_md.char_props.notify = 0;
char_md.p_char_user_desc = NULL;
char_md.p_char_pf = NULL;
char_md.p_user_desc_md = NULL;
char_md.p_cccd_md = NULL;
char_md.p_sccd_md = NULL;
memset(&attr_md, 0, sizeof(attr_md));
attr_md.read_perm = p_cus_init->custom_value_char_attr_md.read_perm;
attr_md.write_perm = p_cus_init->custom_value_char_attr_md.write_perm;
attr_md.read_perm.lv = 2;
attr_md.write_perm.sm = 2;
attr_md.vloc = BLE_GATTS_VLOC_STACK;
attr_md.rd_auth = 0;
attr_md.wr_auth = 0;
attr_md.vlen = 0;
/* This code belongs in custom_value_char_add() in ble_cus.c*/
ble_uuid.type = p_cus->uuid_type;
ble_uuid.uuid = CUSTOM_VALUE_CHAR_UUID;
/* This code belongs in custom_value_char_add() in ble_cus.c*/
memset(&attr_char_value, 0, sizeof(attr_char_value));
attr_char_value.p_uuid = &ble_uuid;
attr_char_value.p_attr_md = &attr_md;
attr_char_value.init_len = sizeof(uint8_t);
attr_char_value.init_offs = 0;
attr_char_value.max_len = sizeof(uint8_t);
/* This code belongs in custom_value_char_add() in ble_cus.c*/
err_code = sd_ble_gatts_characteristic_add(p_cus->service_handle, &char_md,
&attr_char_value,
&p_cus->custom_value_handles_2);
if (err_code != NRF_SUCCESS)
{
return err_code;
}
return NRF_SUCCESS;
}
attr_md.read_perm.lv = 2;
attr_md.write_perm.sm = 2;
No. You can take a look at Heart Rate Application use Just Work pair and secure characteristics as
static inline void set_security_req(security_req_t level, ble_gap_conn_sec_mode_t * p_perm)
{
BLE_GAP_CONN_SEC_MODE_SET_NO_ACCESS(p_perm);
switch (level)
{
case SEC_NO_ACCESS:
BLE_GAP_CONN_SEC_MODE_SET_NO_ACCESS(p_perm);
break;
case SEC_OPEN:
BLE_GAP_CONN_SEC_MODE_SET_OPEN(p_perm);
break;
case SEC_JUST_WORKS:
BLE_GAP_CONN_SEC_MODE_SET_ENC_NO_MITM(p_perm);
break;
case SEC_MITM:
BLE_GAP_CONN_SEC_MODE_SET_ENC_WITH_MITM(p_perm);
break;
case SEC_SIGNED:
BLE_GAP_CONN_SEC_MODE_SET_SIGNED_NO_MITM(p_perm);
break;
case SEC_SIGNED_MITM:
BLE_GAP_CONN_SEC_MODE_SET_SIGNED_WITH_MITM(p_perm);
break;
}
return;
}
If you want the device to send the pairing request to mobile to allow pairing, you can add the code in the BLE_GAP_EVT_CONNECTED event. If the users cancel the pairing request from the peripheral on mobile, they cannot read/write characteristics.
case BLE_GAP_EVT_CONNECTED:
NRF_LOG_INFO("Connected.");
err_code = bsp_indication_set(BSP_INDICATE_CONNECTED);
APP_ERROR_CHECK(err_code);
m_conn_handle = p_ble_evt->evt.gap_evt.conn_handle;
err_code = nrf_ble_qwr_conn_handle_assign(&m_qwr, m_conn_handle);
APP_ERROR_CHECK(err_code);
// send a security request to the peer (master)
ret_code_t err = pm_conn_secure(m_conn_handle, false);
NRF_LOG_RAW_INFO("%s: send secure connection request - err %d\r\n", (int) __func__, err);
if (err != NRF_ERROR_INVALID_STATE)
{
APP_ERROR_CHECK(err);
}
break;
-Amanda H.
Hi Amanda Hsieh
No. You can take a look at Heart Rate Application use Just Work pair and secure characteristics as
I have added in mentioned code in the main.c but getting an error
(static declaration of 'set_security_req' follows non-static declaration).
So I changed like this.
static void gap_params_init(void)
{
ret_code_t err_code;
ble_gap_conn_params_t gap_conn_params;
ble_gap_conn_sec_mode_t sec_mode;
security_req_t level;
BLE_GAP_CONN_SEC_MODE_SET_OPEN(&sec_mode);
err_code = sd_ble_gap_device_name_set(&sec_mode,
(const uint8_t *)DEVICE_NAME,
strlen(DEVICE_NAME));
APP_ERROR_CHECK(err_code);
/* YOUR_JOB: Use an appearance value matching the application's use case.
err_code = sd_ble_gap_appearance_set(BLE_APPEARANCE_);
APP_ERROR_CHECK(err_code); */
memset(&gap_conn_params, 0, sizeof(gap_conn_params));
gap_conn_params.min_conn_interval = MIN_CONN_INTERVAL;
gap_conn_params.max_conn_interval = MAX_CONN_INTERVAL;
gap_conn_params.slave_latency = SLAVE_LATENCY;
gap_conn_params.conn_sup_timeout = CONN_SUP_TIMEOUT;
err_code = sd_ble_gap_ppcp_set(&gap_conn_params);
APP_ERROR_CHECK(err_code);
ble_gap_conn_sec_mode_t * p_perm;
p_perm->lv=2;
p_perm->sm=2;
set_security_req_1(SEC_JUST_WORKS,p_perm);
}
void set_security_req_1(security_req_t level, ble_gap_conn_sec_mode_t * p_perm)
{
BLE_GAP_CONN_SEC_MODE_SET_NO_ACCESS(p_perm);
switch (level)
{
case SEC_NO_ACCESS:
BLE_GAP_CONN_SEC_MODE_SET_NO_ACCESS(p_perm);
break;
case SEC_OPEN:
BLE_GAP_CONN_SEC_MODE_SET_OPEN(p_perm);
break;
case SEC_JUST_WORKS:
BLE_GAP_CONN_SEC_MODE_SET_ENC_NO_MITM(p_perm);
break;
case SEC_MITM:
BLE_GAP_CONN_SEC_MODE_SET_ENC_WITH_MITM(p_perm);
break;
case SEC_SIGNED:
BLE_GAP_CONN_SEC_MODE_SET_SIGNED_NO_MITM(p_perm);
break;
case SEC_SIGNED_MITM:
BLE_GAP_CONN_SEC_MODE_SET_SIGNED_WITH_MITM(p_perm);
break;
}
return;
}
If you want the device to send the pairing request to mobile to allow pairing, you can add the code in the BLE_GAP_EVT_CONNECTED event. If the users cancel the pairing request from the peripheral on mobile, they cannot read/write characteristics.
When I connect the device I get the following error.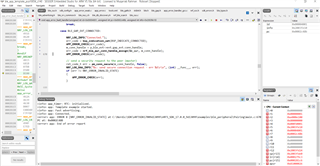
Hi Amanda Hsieh
No. You can take a look at Heart Rate Application use Just Work pair and secure characteristics as
I have added in mentioned code in the main.c but getting an error
(static declaration of 'set_security_req' follows non-static declaration).
So I changed like this.
static void gap_params_init(void)
{
ret_code_t err_code;
ble_gap_conn_params_t gap_conn_params;
ble_gap_conn_sec_mode_t sec_mode;
security_req_t level;
BLE_GAP_CONN_SEC_MODE_SET_OPEN(&sec_mode);
err_code = sd_ble_gap_device_name_set(&sec_mode,
(const uint8_t *)DEVICE_NAME,
strlen(DEVICE_NAME));
APP_ERROR_CHECK(err_code);
/* YOUR_JOB: Use an appearance value matching the application's use case.
err_code = sd_ble_gap_appearance_set(BLE_APPEARANCE_);
APP_ERROR_CHECK(err_code); */
memset(&gap_conn_params, 0, sizeof(gap_conn_params));
gap_conn_params.min_conn_interval = MIN_CONN_INTERVAL;
gap_conn_params.max_conn_interval = MAX_CONN_INTERVAL;
gap_conn_params.slave_latency = SLAVE_LATENCY;
gap_conn_params.conn_sup_timeout = CONN_SUP_TIMEOUT;
err_code = sd_ble_gap_ppcp_set(&gap_conn_params);
APP_ERROR_CHECK(err_code);
ble_gap_conn_sec_mode_t * p_perm;
p_perm->lv=2;
p_perm->sm=2;
set_security_req_1(SEC_JUST_WORKS,p_perm);
}
void set_security_req_1(security_req_t level, ble_gap_conn_sec_mode_t * p_perm)
{
BLE_GAP_CONN_SEC_MODE_SET_NO_ACCESS(p_perm);
switch (level)
{
case SEC_NO_ACCESS:
BLE_GAP_CONN_SEC_MODE_SET_NO_ACCESS(p_perm);
break;
case SEC_OPEN:
BLE_GAP_CONN_SEC_MODE_SET_OPEN(p_perm);
break;
case SEC_JUST_WORKS:
BLE_GAP_CONN_SEC_MODE_SET_ENC_NO_MITM(p_perm);
break;
case SEC_MITM:
BLE_GAP_CONN_SEC_MODE_SET_ENC_WITH_MITM(p_perm);
break;
case SEC_SIGNED:
BLE_GAP_CONN_SEC_MODE_SET_SIGNED_NO_MITM(p_perm);
break;
case SEC_SIGNED_MITM:
BLE_GAP_CONN_SEC_MODE_SET_SIGNED_WITH_MITM(p_perm);
break;
}
return;
}
If you want the device to send the pairing request to mobile to allow pairing, you can add the code in the BLE_GAP_EVT_CONNECTED event. If the users cancel the pairing request from the peripheral on mobile, they cannot read/write characteristics.
When I connect the device I get the following error.