Hello! I will try to make this as simple as possible with the details regarding this issue
What I have
- nRF52840 DK (pca10056) (As BLE sniffer)
- nRF52 (pca10040) (Used in the nRF Connect win10 application)
- Raspberry Pi 4
- OMRON BP7350 BPM
- Hope (just kidding)
One thing to have in mind
Whenever I test this with my phone in the nRF Connect for mobile or in the native OMRON Connect US application this process works perfectly, I am able to connect, pair and read blood pressure data from the sensor.
Description
I am working with an OMRON BP7350 BPM Sensor trying to read blood pressure data from it and I have problems with pairing process using the nRF Connect v3.6.0 - Bluetooth Low Energy application, but basically in order to get data from the BPM is required to connect to it and pair to be able to access to their blood pressure service/characteristics. At this point I have tested a lot of different use cases without success.
My main purpose is to get it to work in the Raspberry Pi 4 but this issue happens also in the nRF52 (PCA10040) and nRF52840 (PCA10056) (I tried backwards) so I think that this might lead me to solve the issue in the raspberry pi (perhaps?).
In the Pi I have bluez v5.50, in the nRF BLE application tool the version is v2.4.2.
And whenever I tried pairing in the Pi 4 or in the nRF52 board BLE application I have this:
> ACL Data RX: Handle 64 flags 0x02 dlen 6 #20 [hci0] 26.420475
SMP: Pairing Failed (0x05) len 1
Reason: Unspecified reason (0x08)
This also happens with another devices like in WIN10 with virtual machines with Debian with bluez, Fedora linux OS, all of them testing with bluetoothctl
which is the same tool that I use in the Pi 4.
What I have tried
For debugging I used the nRF Connect for Mobile application and there I am able to bond/pair to the device successfully with my android and do whatever I want, I am also able to sniff this communication process using wireshark and nRF52 board that I have.
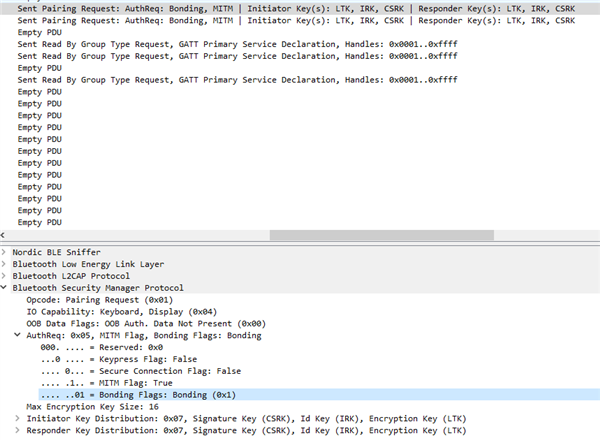
First the request from nRF Connect in my android device to "bond"

And here is the response from BPM

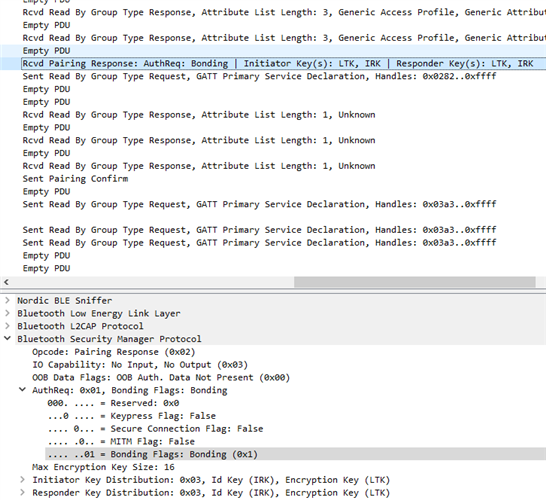
BUT when I do the pairing process with my raspberry pi 4 (And the nRF52) the connection fails with an "Unspecified Reason"

The Response from the BPM

I used sudo btmon to monitor the behavior inside the Raspberry Pi
> ACL Data RX: Handle 64 flags 0x02 dlen 6 #17 [hci0] 26.323537
SMP: Security Request (0x0b) len 1
Authentication requirement: Bonding, No MITM, Legacy, No Keypresses (0x01)
< ACL Data TX: Handle 64 flags 0x00 dlen 11 #18 [hci0] 26.323661
SMP: Pairing Request (0x01) len 6
IO capability: NoInputNoOutput (0x03)
OOB data: Authentication data not present (0x00)
Authentication requirement: Bonding, No MITM, Legacy, No Keypresses (0x01)
Max encryption key size: 16
Initiator key distribution: EncKey Sign (0x05)
Responder key distribution: EncKey IdKey Sign (0x07)
> HCI Event: Number of Completed Packets (0x13) plen 5 #19 [hci0] 26.371976
Num handles: 1
Handle: 64
Count: 2
> ACL Data RX: Handle 64 flags 0x02 dlen 6 #20 [hci0] 26.420475
SMP: Pairing Failed (0x05) len 1
Reason: Unspecified reason (0x08)
I also tested to pair with the GUI tool and gatttool, no success.
-----------------------------------------------------------------------------------------------
And of course, this is the response from the nRF BLE application everytime I tried to pair:
Authentication failed with status BLE_GAP_SEC_STATUS_UNSPECIFIED
I also tried to reproduce the same requirements as the android appears to share with the BPM in terms of:
- IO Capability: Keyboard, Display (0x04)
- AuthReq: 0x05, MITM Flag, Boding Flags: Bonding
This with always a pairing failed response...
Conclusion
So I honestly would like to know what do you think I might need to do to be able to pair successfully the raspberry pi with this BPM device. Do you know what exactly means the "Unspecified reason (0x08)" or what is required to change when you have a Pairing Failed (0x05) in the SMP?
I honestly do not understand how the Initiator Key(s) / Responder Key(s) works and how are able to be changed in order to make work this communication process as I need in the nRF52 with the BLE application, is this something more "device specific"?
From my point of view, there is something in the security layer that is not ending to be completed to achieve a completed pairing process... But I don't know what is it yet
Any suggestion will be helpful on issue. Thank you for your time.