I am trying to set up communication between NRF52840 DK and Raspberry Pi 3 using CoAP example given in NRF SDK's IoT examples.
My configuration:
NRF52840 DK - IPv6 CoAP client example from SDK
Raspberry Pi 3 - BLE 6LoWPAN router and CoAP server with CoAPthon3
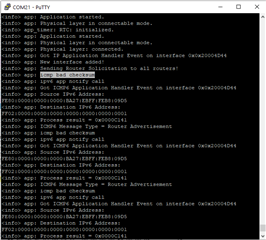
I am able to setup Raspberry as border router for BLE 6LoWPAN. I can run CoAP server using CoAPthon3 on IPv6 (including bt0 interface) successfully. I have added global/unique local IPv6 address on bt0 interface on Raspberry Pi. I am able to connect NRF52840 DK and raspberry Pi using 6LoWPAN over BLE. I have installed radvd daemon for advertising packets. It is transmitting the ICMPv6 packets but with checksum error as captured by wireshark on raspberry pi and also verified by debugging in the NRF52840 CoAP client code. So, client has not been assigned IPv6 address other than link local. As a result, when I make a CoAP request using button 1 or button 2 on NRF52840 DK, it is captured by wireshark but no forwarded to CoAP server
Steps to reproduce the problem:
1. Setup Raspberry Pi as 6LoWPAN over BLE router using
(b) https://github.com/NordicSemiconductor/Linux-ble-6lowpan-joiner
In these steps, I have set radvd configuration file using "sudo nano /etc/radvd.conf" as
interface bt0
{
AdvSendAdvert on;
prefix fd00:a::/64
{
AdvOnLink off;
AdvAutonomous on;
AdvRouterAddr on;
};
};
and assigned raspberry pi bt0 interface with prefix using "sudo ifconfig bt0 add fd00:a::1/64"
2. Setup CoAP server on Raspberry Pi using Coapthon (github.com/.../CoAPthon3).
(a) clone the repository on raspberry pi (git clone https://github.com/Tanganelli/CoAPthon3.git)
(b) open coapserver.py and change server IPv6 address in the main function as
def main(argv): # pragma: no cover
ip = "::"
port = 5683
(c) run server file from the terminal (python3 coapserver.py)
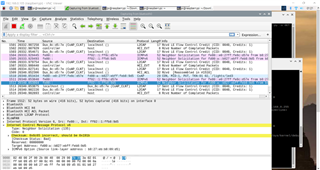
3. Checking the CoAP server by running CoAP client on Raspberry Pi terminal using same Coapthon repository (working fine - screenshots attached):
(a) using wlan0 IPv6 localhost - sudo python3 coapclient.py -o GET -p coap://[::1]:5683/basic -P "test payload"
(b) using wlan0 inet6 link local address - sudo python3 coapclient.py -o GET -p coap://[fe80::fc47:97f7:14dc:aaa3]:5683/basic -P "test payload"
(c) using bt0 link local address - sudo python3 coapclient.py -o GET -p coap://[fe80::b827:ebff:feb8:9d5]:5683/basic -P "test payload"
(d) using bt0 global/unique local address - sudo python3 coapclient.py -o GET -p coap://[fd00:a::1]:5683/basic -P "test payload"
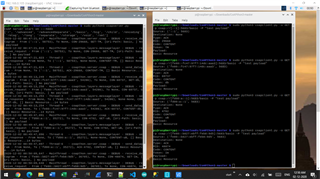
4. Checking the CoAP server from NRF52840 DK client
(a) change the server address to raspberry pi bt0 address (fd00:a::1) in examples\iot\coap\ipv6\client\main.c file
change the code in icmp6.c to add NRF_LOG_INFO("icmp bad checksum") statement for debuging purpose as shown below in function icmp6_input:
if (checksum != 0)
{
NRF_LOG_INFO("icmp bad checksum");
ICMP6_ERR("Bad checksum detected. Got 0x%08x but expected 0x%08x, 0x%08lX",
NTOHS(p_icmp_header->checksum), checksum, p_packet->length);
process_result = ICMP6_BAD_CHECKSUM;
}
(b) upload the IPv6 coap client code using nrf Connect Programmer
(c) connect NRF52840 DK using terminal command "echo "connect 00:E0:27:8C:D5:7E 1" > /sys/kernel/debug/bluetooth/6lowpan_control"
where mac address of NRF52840 comes from scanning command on terminal "hcitool lescan"
(d) check using termincal command "hcitool con"
(e) press button 1 or button 2 on to send CoAP request to the server (captured on wireshark - screenshot attached) but not forwarding to coap server
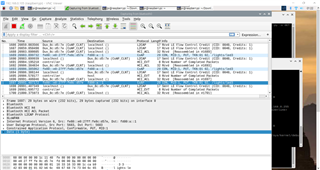
(f) advertisement packet from radvd is showing checksum error (wireshark screenshot and NRF 52840 PuTTY screenshot attached)