SDK: 4.1.0
CHIP: nRF52840
ROLE: sleepy zed
GATEWAY: third party ember stack
old question
old story:
- Issue: Doesn't update network key - 4.6.3.4 Network Key Update in zigbee spec.
- The current procedure of updating network key:
1) The gateway periodically changes the network key.
2) After changing the network key, The gateway doesn't receive the message encrypted with old key from the zed.
3) The zed doesn't receive APS ACK to the period request.
4) Since zed does not receive a response, it assumes that the network key has changed.
5) The zed request the rejoin message without encryption.
6) The gateway accepts unsecured rejoin .
7) The gateway send "Transport Key" encrypted with ZB_STANDARD_TC_KEY which is the same as when joining.
8) The zed processes this message and updates the network key.
It is the procedure of updating the network key has the gateway.
I has succeed until "5) requesting unsecured rejoining".
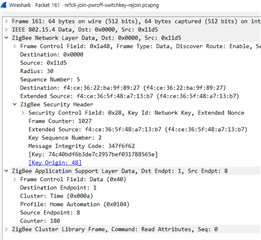
so, I received "Transport Key" encrypted with ZB_STANDARD_TC_KEY.
However, the zed does nothing. It doesn't even seem to be decryption of "Transport Key" message.
I watched the functions "nrf_802154_received_timestamp_raw" it was called and "hw_aes128" it wasn't called.
this is pairing procedure.
this is rejoining procedure.
there are keys for pcap.
ZB_STANDARD_TC_KEY
5A:69:67:42:65:65:41:6C:6C:69:61:6E:63:65:30:39
Current Gateway key - not necessary
7F:94:FE:28:95:41:48:83:F9:16:F2:2D:8D:4B:78:97
How can I reach the goal?
1) If I terminate the old key, Does the zed receive "Transport Key" message?
2) How can I get or delete the network keys? I can't find the related api.
I already use "zb_bdb_reset_via_local_action" function to erase all parameter. I wants to terminate only network key to rejoining the network.
3) I uses IAS zone cluster. Is it related on this issue? I found the post.
"The reason the Elko PIR sensor does not retrieve the key is because it uses a cluster called IAS Zone, which gives extra security for the device, and has an extra step in the commissioning process." what is meaning? Why is IAS ZONE CLUSTER related to zigbee network security?

.
case ZB_ZDO_SIGNAL_SKIP_STARTUP: {
/* At this point Zigbee stack:
* - Initialized the scheduler.
* - Initialized and read NVRAM configuration.
* - Initialized all stack-related global variables.
*
* Next step: perform BDB initialization procedure (see BDB specification section 7.1).
*/
m_stack_initialised = ZB_TRUE;
zb_disable_nwk_security();
DEBUG_PRINTF("Zigbee stack initialized\n");
DEBUG_PRINTF("bdb_start_top_level_commissioning\n");
zb_secur_set_tc_rejoin_enabled(ZB_TRUE);
comm_status = bdb_start_top_level_commissioning(
// ZB_BDB_INITIALIZATION | ZB_BDB_TOUCHLINK_TARGET | ZB_BDB_REJOIN
ZB_BDB_INITIALIZATION
);
DEBUG_PRINTF("initialized zb_bdb_is_factory_new(): %d\r\n", zb_bdb_is_factory_new());
/* WORKAROUND for the ZOI-297: unlock the device's address on ZEDs to fix assertion upon leave request. */
zb_address_ieee_ref_t addr_ref;
/* Unlock our address: it will be locked at rejoin confirm */
if (zb_address_by_short(ZB_PIBCACHE_NETWORK_ADDRESS(), ZB_FALSE, ZB_FALSE, &addr_ref) == RET_OK) {
zb_address_unlock(addr_ref);
}
} break;


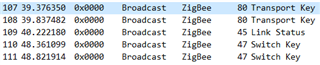
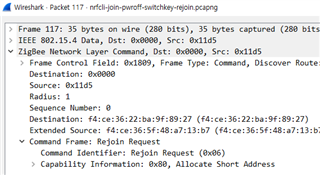
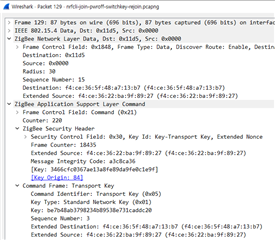
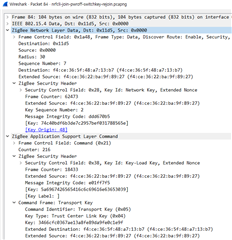 -> Trust Center Link Key In Joining
-> Trust Center Link Key In Joining