I am currently working on a project involving passing sensor data to Microsoft Azure.
I am looking at the sample application v1.4.99-dev1/nrf/samples/nrf9160/azure_iot_hub currently.
I just got v1.5.0 installed, had to delete and restart the install a few times (MacOS) due to incomplete/incomplete downloads/installs, but finally have a full install and will switch over to v1.5.0 as time permits. Download and install takes about 4 hours (each attempt).
I have been digging through the documentation and the forums for a bit and would like a little clarification on a few points.
Currently we use a Raspberry Pi to upload data to Azure, the Raspberry Pi is automatically provisioned by downloading an X509 certificate from a self developed PHP server that generates and signs device certificates with the CA that is registered with the Azure device provisioning service. Provisioning a Raspberry Pi is as easy as booting it with a special provisioning SD card and it automatically downloads it's unique device certificate and stores it locally in an EEPROM chip.
I am attempting to create a similar kind of auto provisioning system for the nRF9160 is it is time consuming to do this provisioning by hand. This has brought up a few questions.
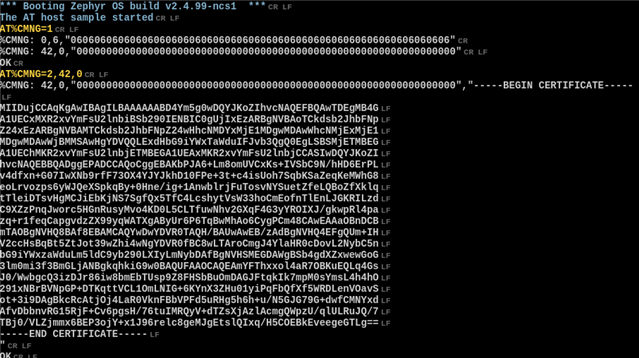
1. From looking at the sample source I am under the impression that this uses the MQTT library. This also appears to use the TLS certificate store as the function "tls_credential_add" is called. Is it possible to use a certificate loaded into SRAM? As the certificate is quite a few bytes long this may not be exactly efficient.
2. I am planning on storing the certificates on an external SD card as they are downloaded from the automatic provisioning server, but ultimately they may need to be stored in the nRF9160's TLS certificate store. I am concerned about write wear on the EEPROM memory used for the certificate store, is there any concern? Has there been any testing as to what kind of endurance there is for this memory? I am sure it is somewhere in the nRF9160 datasheet but I have not been able to locate the information as of yet. I am always a little paranoid about write endurance on things like EEPROM, SD cards, and SSD memory devices since they will be out in the field where failure is a really bad thing. The above mentioned Raspberry Pi SD card root filesystem is setup in a read-only mode for this reason.
3. If the X509 certificate is stored in the TLS store, is it possible to read back, or compare it to what is stored on the SD card, if I go with using the SD card as the primary storage location for the X509 certificates I would like to rewrite the certificate stored in the TLS store on startup, but don't want to rewrite it if unnecessary to avoid wear on the EEPROM memory. Is there logic in the TLS writing logic that would compare what is in EEPROM and only erase/write bytes that have changes (to avoid wear)? I incorporate similar logic in the Raspberry Pi EEPROM writing logic.
4. I believe this is not a question of possibility, but development time, but I would like to add in the ability in this project for the nRF9160 to directly download the X509 certificates using HTTP (HTTPS). Concerning the HTTPS, does the server certificate or root CA need to be registered for an HTTPS connection to be established? Concern with this is the server's SSL certificate is renewed every 3 months.
5. This is outside of the scope of Azure, but I will need to store APN information (authentication included) for the SIM cards that will be used, the MVNO SIM cards that I have been using do not really cooperate with the automatic APN feature of the nRF9160 and therefore will be storing this information on the SD card anyway, so figured I might as well store the X509 certificates as well on the SD card.
6. In the event that Azure does not connect, an automatic download of a new X509 certificate and connection attempt might be made each time power is cycled, in this case I don't want to cause write wear on the TLS certificate store, if it can be avoided. If the certificate must be in the TLS certificate store to be used by Azure this might not be avoidable so after some failed attempts a flag might have to be set for service. Again concerned about the EEPROM wear.
7. I guess what I am really looking for is some advice on a smooth method to auto provision the nRF9160 for Azure, with the possibility that the X509 certificates will need some method to be updated in the field when the device is in the customer's hands. As seen from the Raspberry Pi scenario auto downloading of device specific X509 provisioning certificates has been implemented and looking for a smooth provisioning method for the nRF9160 so any advice on this would be helpful.