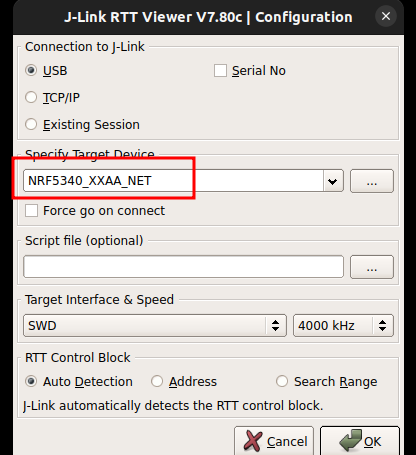
Working in a Windows 64 environment with nRF Connect SDK v1.5.0. Target is a custom nRF5340 board connected through a nRF5340-PDK as a debugger, via USB.
I can no longer use RTT Viewer to connect to our target: any attempt to connect pops up a message saying CTRL-AP indicates that the device is secured... Do you want to unsecure the device?
Answering YES fully erases the target. Answering NO results in denied connection.
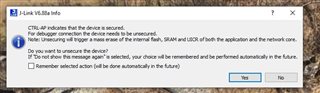
The same message is popping up when trying to run the debugger directly via Segger (the debugger works, but only after it fully erased the target and reuploaded the code).
This was not happening before, but we are unsure of what was changed to cause it and how to get around.
Regards
Bruno