Hi,
I'm getting error on connect to cloud server (socket.nouslogic.com:443) with error code is 45 ( EOPNOTSUPP).
Here are detail:
1. Using https_client example on nRF Connect NCS v1.5.0, modem_fw 1.1.4, network mode is NB-IoT on nRF9160 DK
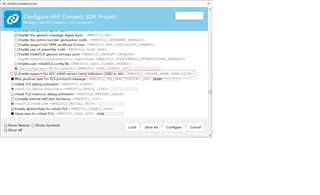
2. Set TLS_PEER_VERIFY via "verify" value to NONE ( =0) to discard the certificate verifying ( eliminate wrong certificate file)
3. Host is "socket.nouslogic.com", this is custom CNAME on Amazon CloudFront, configured with SNI option.
4. Certificates is root CA from "openssl s_client -showcerts -tls1_2 -connect socket.nouslogic.com:443". (We did try to support 3 certificate chain in 3 different security tags also)
5. In configuration, select mbedtls support( zephyr built-in) to enable the SNI option. ( tried enable all cipher suites as well)
Result:
- other sites work well: google.com, amazon.com or any website without CloudFront configured (tested with vn.yahoo.com, vnexpress.net, mqtt.eclipseprojects.io ( correct certificate))
- our cloudfront host ( socket.nouslogic.com) or "nrfcloud.com" or even direct domain "dsmatvilvjgnu.cloudfront.net": connect fail with error 45.
Question:
- Does NCS v1.5.0 support TLS/SSL connection to Amazon CloudFront yet?
- If above question is YES, so please help to solve the problem.
- If you have any example that successfully connect to our site ( socket.nouslogic.com:443) or any CloudFront site , please share the configuration file or source code.
Thanks in advance.
Best Regards.
Viet Nguyen