Hello everyone,
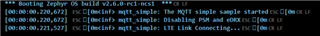
I started an evaluation for the Nordic Thingy91 using the "mqtt_simple" example from the SDK1.6.0 version. The Thingy91 is HW-version 1.4.0. Programming is done in SES V5.50c.
The standard-example works (which connects to mqtt.eclipseprojects.io).
I tried to connect to another server without a username and a password and it also worked as intended. I did this by changing the "MQTT_BROKER_HOSTNAME" in Kconfig and the "CONFIG_MQTT_BROKER_HOSTNAME" in prj.conf. I know, only the prj.conf needs to be changed, I changed both to be sure.
Then I changed the host a server which need a specific username or a password. TLS is not used.
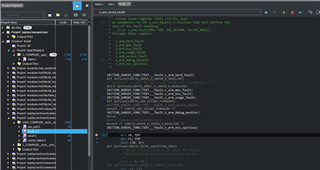
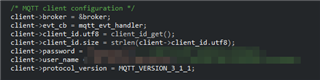
I added the username and password in the main.c:
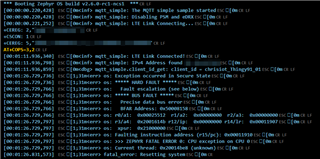
The result is "mqtt_connect -12":
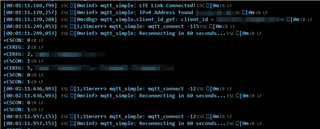
I found this topic (mqtt connect error - Nordic Q&A - Nordic DevZone - Nordic DevZone (nordicsemi.com)) and increased the buffer size in the prj.conf and Kconfig to 512:
CONFIG_MQTT_MESSAGE_BUFFER_SIZE=512
CONFIG_MQTT_PAYLOAD_BUFFER_SIZE=512
In the mentioned topic, the connect error -12 was solved by increasing buffer sizes. For me, the problem persisted, as shown in the second picture.
What can I do to find the error?
With other MQTT Clients I can connect to the server using the same username and password,