Hi Sir/Miss,
I try to implement static passkey in my project. Which is using nRF52810.
The SDK version is 17.0.2.
Softdevice is S112.
My project is based to develop on NUS.
I want to use central device to enter passkey to do pairing and bonding.
It's just like ble_app_gls example.
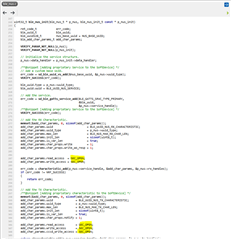
I refer ble_app_template example to add peer_manager and fds in project.
Reference this to do it.
#define SEC_PARAM_BOND 1 /**< Perform bonding. */ #define SEC_PARAM_MITM 1 /**< Man In The Middle protection required (applicable when display module is detected). */ #define SEC_PARAM_LESC 0//1 /**< LE Secure Connections enabled. */ #define SEC_PARAM_KEYPRESS 0 /**< Keypress notifications not enabled. */ #define SEC_PARAM_IO_CAPABILITIES BLE_GAP_IO_CAPS_DISPLAY_ONLY /**< Display I/O capabilities. */ #define SEC_PARAM_OOB 0 /**< Out Of Band data not available. */ #define SEC_PARAM_MIN_KEY_SIZE 7 /**< Minimum encryption key size. */ #define SEC_PARAM_MAX_KEY_SIZE 16 /**< Maximum encryption key size. */
And, add setup static passkey code between ble_stack_init() and advertising_start()
When I use dongle to connect nrf52810 in nRF connect, it doesn't pop up passkey entry window on it. It's connected directly.
It's different with glucose example.
How do I set it up?
Thank you.