Good morning,
We have a new equipment based on the nRF52840 and s140.
Just now, a new problem has appeared and it is very strange, as it seems to be a ‘random’ error:
We have already assembled tens of equipment, and most of them are perfectly working with any smartphone (using both your ‘nRF Connect’ application or our own application).
But, we have a few smartphones that show a strange behavior: they are able to perfectly connect to some of our nRF52840-based equipment, and in a few ones, they are able to connect but they get disconnected after a few seconds. Same equipment is connecting to other smartphones without problems (without disconnecting).
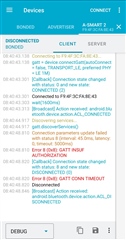
This is (step by step) what it is happening a few times:
- Equipment (nRF52840) is advertising.
- Smartphone stablish connection with equipment using pin number
- First time, the connection is perfectly working.
- If smartphone is disconnected and connected back again with same equipment (Already bonded), then connection is stablished but smartphone disconnects after 30”, approximately. Same behavior is happening with both nRF connect application and our own application. Looking at log in nRF application we see: ‘Connection terminated by peer (status 19)’or ‘GATT_CONN_TIMEOUT’
Why is it happening?
Which is the reason?
How can we solve this?
Could you help us? (For your information, we have set MIN_CONN_INTERVAL to 7.5m and MAX_CONN_INTERVAL to 100ms)
Thank you