After reviewing the add DFU support to your application guide
Add DFU support to your application
i have several questions:
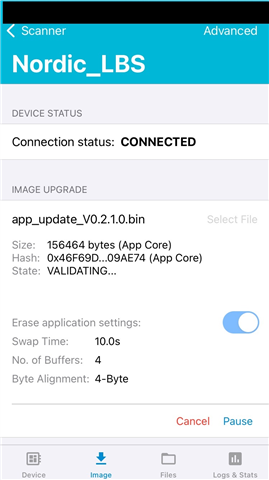
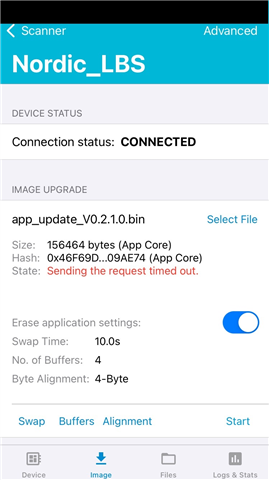
1)What modifications are required for the nRF5340 with an app core and net core? This example shows using Device Manager to upload a .bin file but that is only one of the app core or net core, not both. Can Device Manager accept a the generated .zip with the manifest to update both at once? Could a similar guide be generated for updating both the app and net cores at the same time? When trying to upload the zip of both, Device Manager shows the hash of both bin files, but when started with confirm only, the state shows VALIDATING… for a while then “Sending the request timed out.” When using the advanced page, I can manually select the app core and download the bin for it – not the zip.
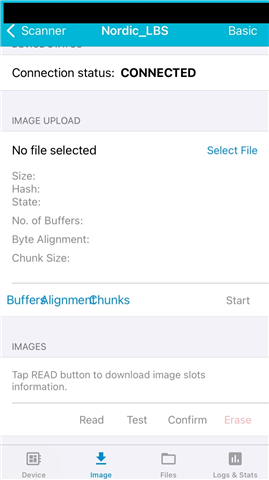
2)In Device Manger, the read, test, confirm, and erase options do not work. How can they be activated?
3)The guide said that Device Manager will reset the device after the transfer but watching the debug output on the device, this is not the case. I need to manually press the advanced button to get the reset command to show then issue it. Is this correct?
4)I have read about encryption and updating keys but in other places it appears it is not supported to encrypt an image:
Please add/enable support for encrypted images with MCUBOOT
Is it correct to say signing is supported but encryption is not? Is there a step by step guide to generate new encryption keys (or signing keys) and update the MCUboot and app for both the app core and net core?
5)If singing is working correctly, is it still possible for a user to upload an image that is not correctly signed, but that the MCUboot will just not swap to it?
Thank you