Hi
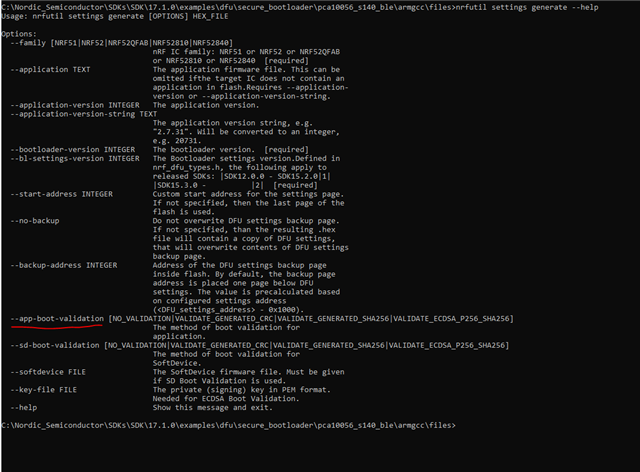
I have a running DFU code and can update the bootloader as generated zip file and the app with the zip file. Now I saw, that there is the option "VALIDATE_ECDSA_P256_SHA256" to generate the packages.
Now I got 2 questions:
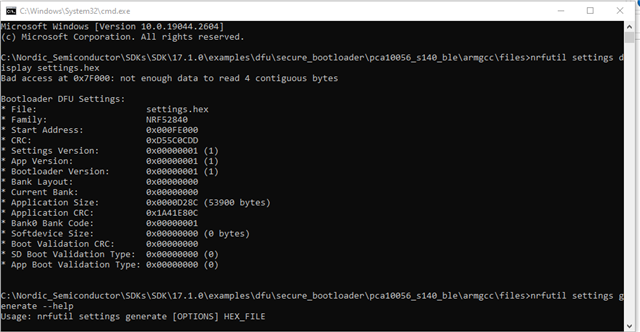
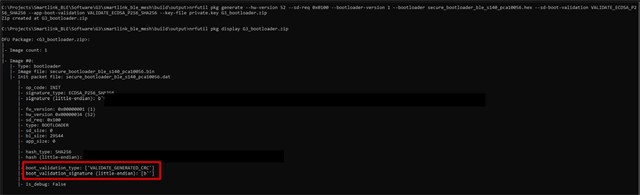
1. I made a test and got the Info from the packages with nrfutil pkg display and saw that to zip file for the bootloader is still with CRC validation, why?
the app is with the correct validation:
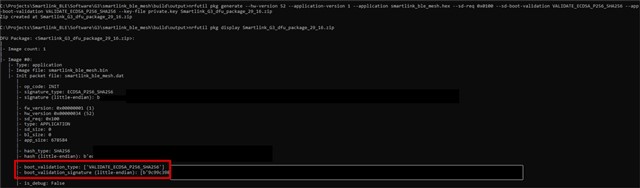
2. If I download the zip package of the APP with the --app-boot-validation VALIDATE_ECDSA_P256_SHA256, its working. But I can still download an App zip file with CRC validation. The same for the bootloader zip file. Why this? Do I have to use the nrfutil settings generate with the option --app-boot-validation and --sd-boot-validation with VALIDATE_ECDSA_P256_SHA256 aswell?
I expected that a zip file without the VALIDATE_ECDSA_P256_SHA256 is not valid and the update would be impossible, which is not the case.
Thanks for a feedback