Hi,
We managed to build and flash SLM (SDK 2.1.2) with Native TLS.
To be able to download about 5Kb of data at one time (from AWS broker).
But not everything works fine, we have several critical problems with this build:
1) First, We can't check certificates, the same we did it before.
Previously, I used commands like this (321, is our internal secure tag):
- AT%CMNG=1,321,0 (For check exists the CA certificate);
- AT%CMNG=1,321,1 (For check exists the Client certificate);
- AT%CMNG=1,321,2 (For check exists the Private Key);
But after moving to Native TLC, and generating the new certificates (via commands like the AT#XCMNG=0,321,0...), We see other certificates by AT%CMNG=1 command:
%CMNG: 3210,0,"AD6FB002E6B34C0559FA8F93A3794FF12C4E3F119BD77290C52525123FB9EA74"
%CMNG: 3211,0,"EA89F71E2A945D88A7A71C3C35D2F3BA5466B0ACEC750270134F511FB0CB4143"
%CMNG: 3212,0,"EB569D288E10B1D9D5B1BD45642AD4B8D063E0C48584A6C3A7A700987D671B68"
Can I use them to verify the CA, Client and private key?
- AT%CMNG=1,3210,0 (For CA);
- AT%CMNG=1,3211,0 (For Client);
- AT%CMNG=1,3212,0 (For check exist the Private Key).
2) Second: We lost access to nRF Cloud.
All commands for working with CMNG had to be changed (was AT%CMNG became AT#XCMNG), and it helped for access to AWS broker, but not to nRF Cloud.
Our previous certificates don't work more (with Native TLS).
I tried to reinstall them using the #XCMNG AT command, but that didn't work.
AT commands and answers look fine.
Maybe this is due to the generation and installation of a private key, we use:
AT%KEYGEN=16842753,2,0\r\n
But after using the
AT%KEYGEN=16842753,2,0\r\n, followed by saving the CA/Client certificates, we have the next results (every install certificate command returned OK):
[7/12 17:55:04:025] %CMNG: 16842753,2,"7494C435C484599577AB9B04E85DD594C5B5C9676750CA6DA17284E99A93B9C7"
[7/12 17:55:04:025] %CMNG: 168427530,0,"AD6FB002E6B34C0559FA8F93A3794FF12C4E3F119BD77290C52525123FB9EA74"
[7/12 17:55:04:025] %CMNG: 168427531,0,"D12494EF17B635B10A7511A513CB37B3101D58008ADE0D4BAA381D85A63DA675"
But if we tried to connect to nRF Cloud nothing happened.
We didn't have some ERROR or Event about the nRF Cloud connection.
We received the OK after about 900ms and CSCON: 0 after 6 seconds.
What are we doing wrong with nRF Cloud access now? Is it still because of the AT%KEYGEN=16842753,2,0 AT command?
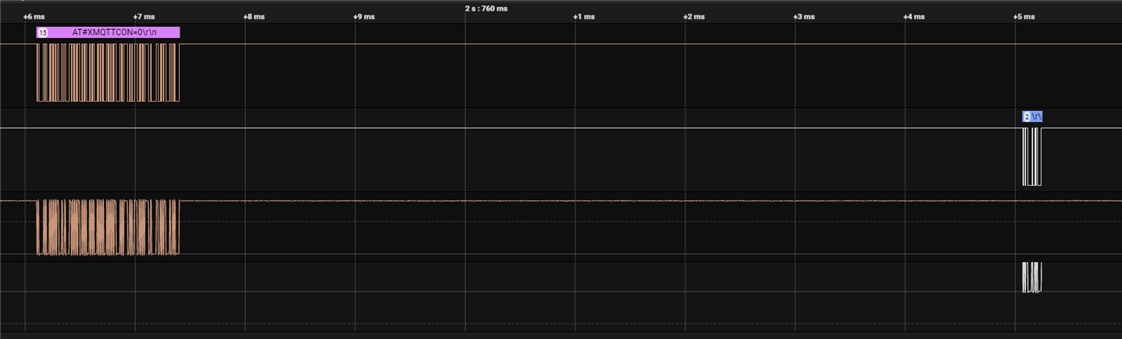
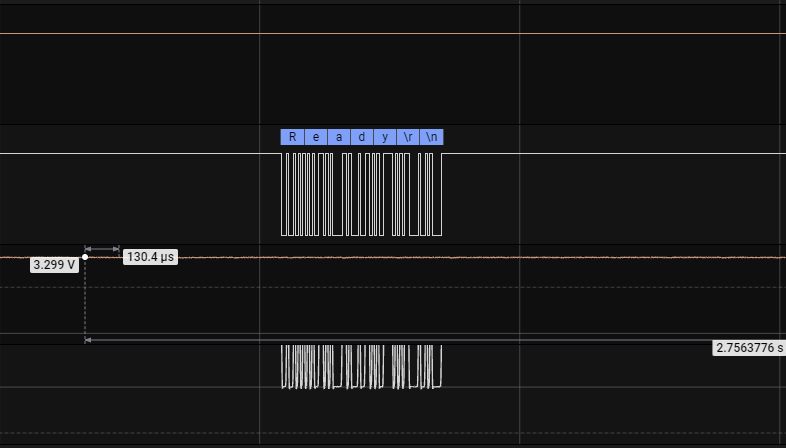
3) Third: Something happening with MQTT Disconnect:
After AT#XMQTTCON=0 we received a weird answer (\r\n) and nRF Reset.
AT#XMQTTCON=0
Ready