Once you pair an nRF52480 devkit running the sample app peripheral_sc_only with the nRF Connect for Desktop Bluetooth Low Energy Standalone tool, you can't reconnect after the initial disconnect.
If instead of the desktop app I use the Android mobile app nRF Connect tool, I don't have that problem. That is, I can bond, disconnect, and then successfully reconnect.
Steps:
1. Build peripheral_sc_only as-is for the nRF52840 devkit.
I am using NCS 2.2.0, but I think the problem has existed since at least 1.9.1.
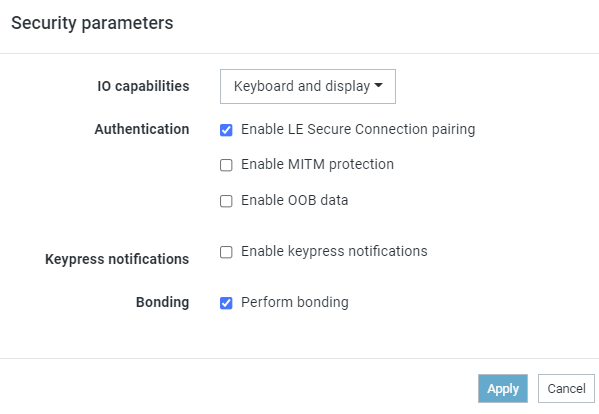
2. Set the desktop BLE tools security parameters as shown below. I am using nRF Connect for Desktop Bluetooth Low Energy Standalone v4.0.0, but I think the problem has existed with many older versions too.
3. Initiate the BLE connect from the BLE tool.
4. In the BLE tool, enter the passcode printed in the peripheral's terminal window.
5. Pairing succeeds. Log from peripheral is as follows:
Connected F6:71:A1:D7:32:D5 (random) Passkey for F6:71:A1:D7:32:D5 (random): 787282 Pairing Complete Security changed: F6:71:A1:D7:32:D5 (random) level 4
6. Initiate disconnect from the BLE tool.
7. Initiate connect from the BLE tool.
8. Connection is attempted but fails.
Log from peripheral is as follows:
Connected F6:71:A1:D7:32:D5 (random) Security failed: F6:71:A1:D7:32:D5 (random) level 1 err 9 Disconnected from F6:71:A1:D7:32:D5 (random) (reason 0x3d)
Note that disconnect reason 0x3d is BT_HCI_ERR_TERM_DUE_TO_MIC_FAIL.
The BLE tool shows a disconnect timeout reason of BLE_HCI_CONNECTION_TIMEOUT.
9. Wireshark shows the following for this reconnect attempt:
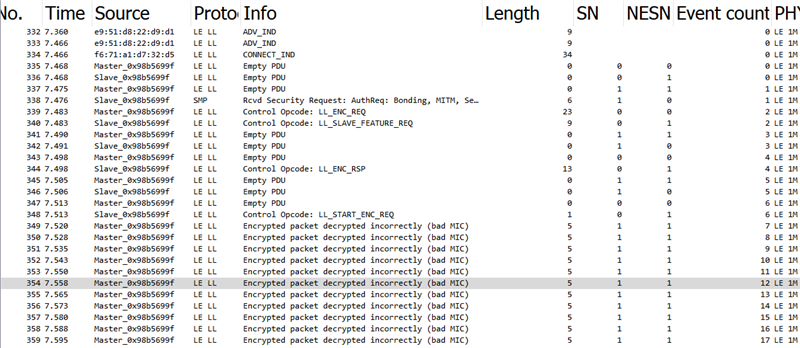
You can see in the Wireshark log that the central (BLE tool) repeatedly sends a packet of length 5 bytes but without any response from the peripheral.
In the sample app, I also enabled printing the sniffer key by setting CONFIG_BT_LOG_SNIFFER_INFO=y. However, even Wireshark is not able to decrypt the encrypted data when I provided it with the SC LTK.


