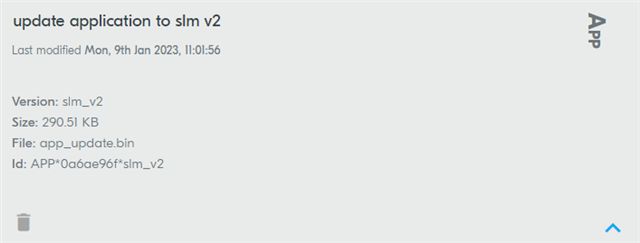
We use nRF9160 with our board (with Serial LTE Modem 1.9.1).
We try to download SLM / Modem firmware via nRF Cloud and we ran into several problems/misunderstandings:
1) First, We cannot add any modem firmware to the bundle.
We received the message that we don't have permission to upload the modem.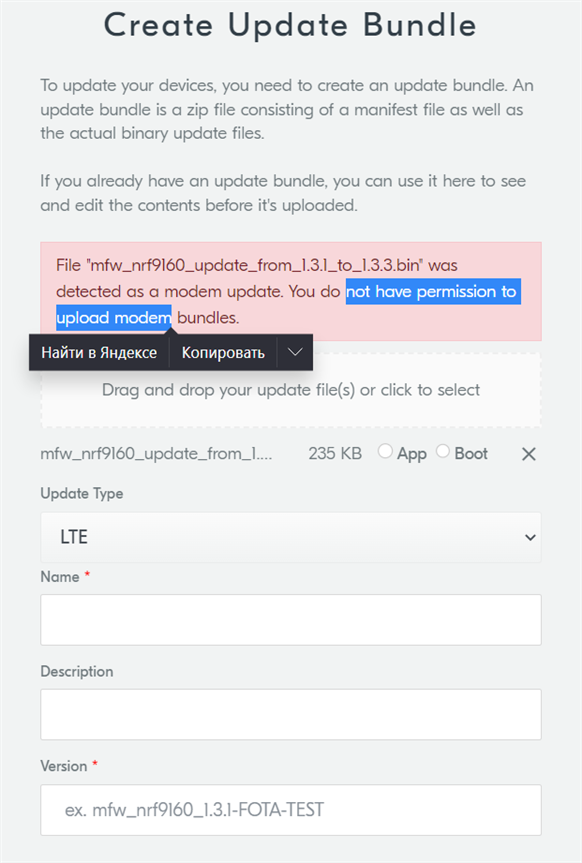
2) Second: If we try to follow your instruction (from "FOTA_AT_commands.rst").
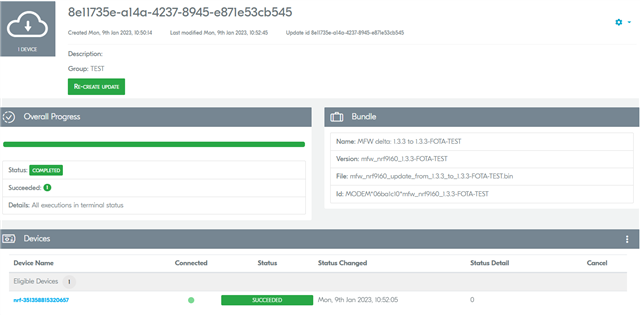
Having previously created the group, bundle, and update, we further waiting that something to happen (status of update: is progress), but nothing happened: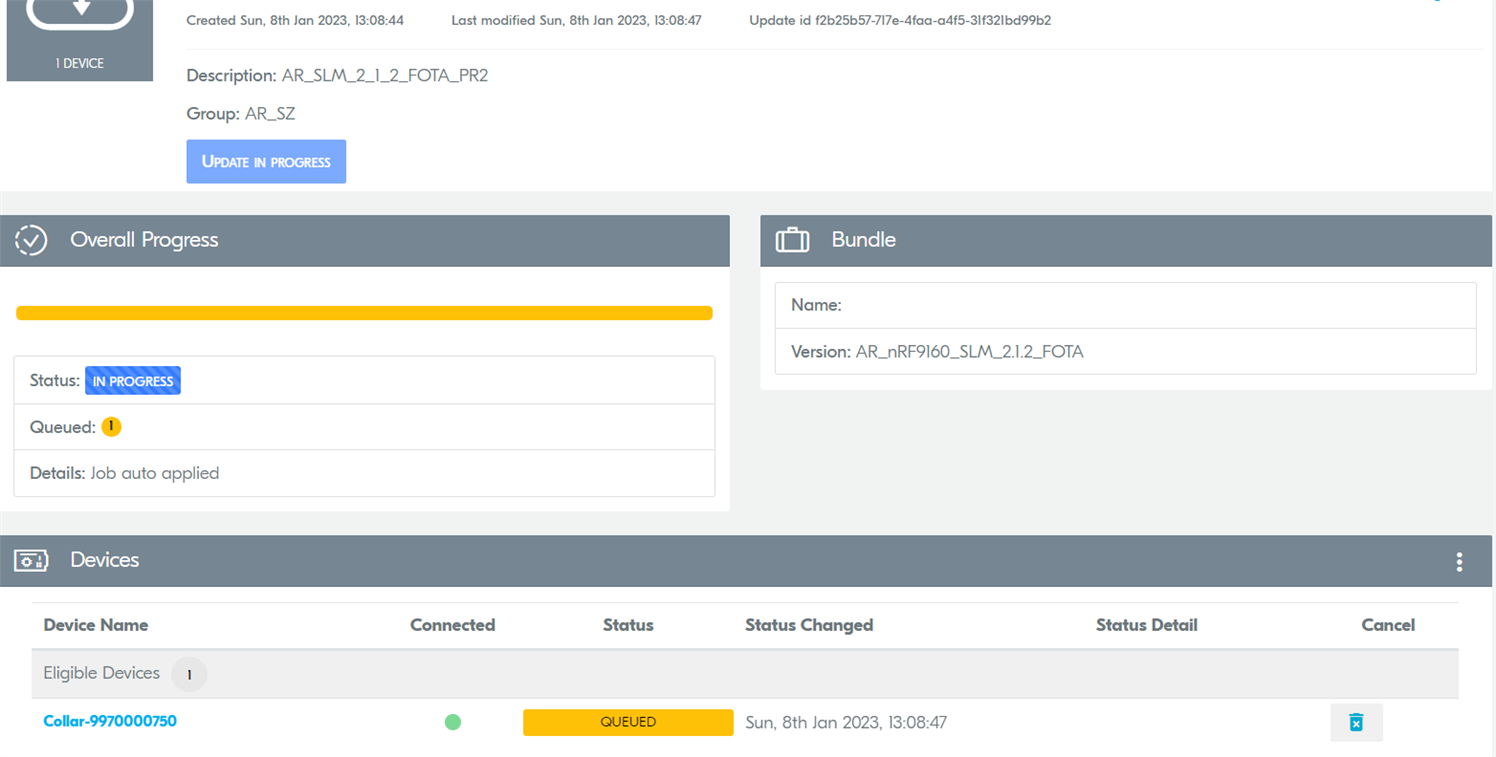
We suggest that the next step should be executed the next AT#XFOTA=1,"<URL of .bin update file>" command.
But where and how we can get the URL address from the created update?
Below I have added a log of AT commands at this moment (We communicate with your module directly via UART TX / RX without our additional logic):
AT+CEREG=5
OK
AT+CFUN=1
OK
+CEREG: 2,"084D","00A52803",7
+CEREG: 5,"084D","00A52803",7,,,"11100000","11100000"
AT#XNRFCLOUD?
#XNRFCLOUD: 0,0,16842753,"50334e33-3135-42c3-80a9-1d170d1621d7"
OK
AT#XNRFCLOUD=1
OK
#XNRFCLOUD: 1,0
AT#XNRFCLOUD?
#XNRFCLOUD: 1,0,16842753,"50334e33-3135-42c3-80a9-1d170d1621d7"
OK
AT#XFOTA=6
#XFOTA: 3,1,353188,"0.0.0+0"
OK