Hi All,
I am currently working on establishing a thread network to communicate to our http server:https://mainnet.incubed.net). In order to setting up that I took echo_client and http_client sample and adapted to our need. Below diagram is my network configuration with RPi connected with ethernet.
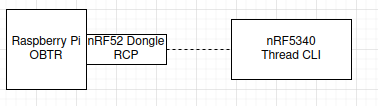
I was successful in pinging the http server from thread network. Here I wanted to send TCP packets to remote server via OT network.
I am novice to networking topics so it is really hard for me to understand and interpret the logs from the thread device. Below given is the log from the one node:
Can someone tell me what is happening here and what I did wrong or not taken into my consideration.
Regards
Vipin Das
