Hi Folks,
SDK17.1.0, MDK8.40.3, S140
My goal is to lock out access to the debug port of an NRF52840-QIAA-T (revision 3), so that the port cannot be used to alter or read the memory of the chip in any way.
1: What is the standard way to include the defintions discussed in IN-141 ("ENABLE_APPROTECT") ? - Do i manually make these definitions? or are they already in a file, waiting to be enabled? similar to the SDK_config.h file?
2: How can I ensure I do not suffer the vulnerability discussed in IN-133?
I found the following blow post: Working with the nRF52 Series' improved APPROTECT
and have reviewed the infocentre: https://infocenter.nordicsemi.com/index.jsp?topic=%2Fcom.nordic.infocenter.nrf52832.ps.v1.1%2Fuicr.html
3: The code listed in this post to set the UICR.APPROTECT register, will this code work standalaone? With no prerequisites required to run the NVMC?
4: What is the MDK licence.msi file for? I installed it to see what would happen... but i'm not clear on it's purpose.
5: Much of the documentation makes reference to the CTRL-AP, I have read the info centre documentation for this. Regardless, what i'd like to know is how one would typically modify these registers, via SWD?
I found quotes such as:
After an ERASEALL operation is executed (by nrfjprog or manually via the CTRL-AP) the device should be accessible to a debugger until it executes a pin, power, or brownout reset.
What does is mean, "manually"? Can someone explain the options for how to issue an ERASEALL operation?
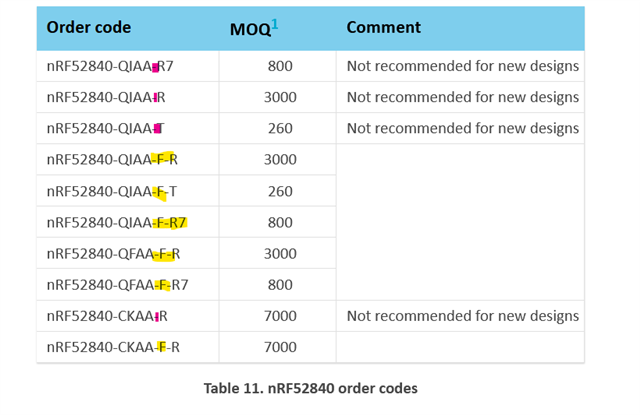
6: I am also seeing some confusing notes on the naming cultures for the build revisions to the chip. Any confirmation that the T model i see with many suppliers is definitely revision 3 would be useful. Exactly what revision is the chip i am seeing advertising as NRF52840-QIAA-T?
Best regards,
Sean
IN-133:
https://infocenter.nordicsemi.com/pdf/in_133_v1.0.pdf
IN-141: