Hi,
I'm working on a legacy program (Peripheral) using nRF52833 and nRF5 SDK using SoftDevice S113.
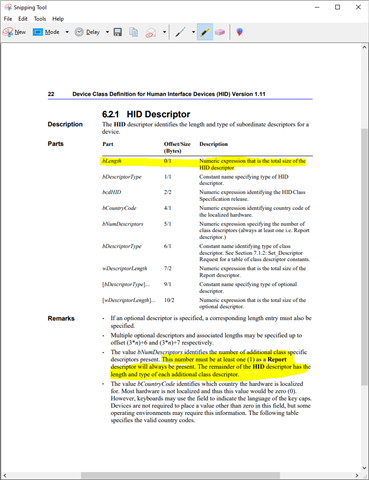
Our application implements an HID device using the Keyboard/Mouse example code from the nRF5 SDK, which leverage the generic ble_hids component that implements HoGP (HID Service).
We see a failure mode where the HID enumeration fails because the GATT Read fails (due to a malformed packet exceeding MTU error). The HID report map (added to the GATT database via rep_map_char_add() ) Characteristic is longer than the negotiated ATT MTU, and the issue does not occur if the HID Report Map size is less than the negotiated MTU.
Are long reads handled internally by the SoftDevice (or other SDK libraries/modules)? Or is the expectation that the App (or ble_hids module) should handle long reads until the full Characteristic is read out (and cap the READ reply to the MTU size to force the Central to request subsequent READ_BLOB operations with offset)?
If it's the latter, does it mean App needs to add handling for every Service/Characteristic, of BLE_GATTS_EVT_RW_AUTHORIZE_REQUEST for each GATT Read, and for each manually return data up to the current MTU?
Looking the HID examples in the SDK, I didn't see any special handling for GATT Read against the MTU (only Gatt Write/Notifications in Heart Rate Service or Nordic UART Service are breaking the Char Notifications in chunks).
Is there something I need to enable in the SDK to allow GATT Read/Write of payloads > MTU, or anything specific at the App layer?
Thanks,
Marco
PS: I found a similar ticket here that describes a similar problem on a custom Service (instead of a standard Service like HID, supported in the nRF5 SDK).