I am trying to setup a secure connection using an IPv6 TLS socket on my nRF9160 device, but it fails with errno=45.
To setup the socket I perform these steps (stripped of logs and such for clarity):
static struct addrinfo hints =
{
.ai_family = AF_INET6,
.ai_socktype = SOCK_STREAM,
};
// get the server address
getaddrinfo("host.name", NULL, &hints, &res);
// add tls credentials
tls_credential_add(CA_CERTIFICATE_TAG, TLS_CREDENTIAL_CA_CERTIFICATE, ca_cert, strlen(ca_cert));
// check that tls credentials are stored
tls_credential_get(CA_CERTIFICATE_TAG, TLS_CREDENTIAL_CA_CERTIFICATE, cert_buf, sizeof(cert_buf));
// configure the port (443)
((struct sockaddr_in *)res->ai_addr)->sin_port = htons(443);
// set tls socket options
sock = socket(AF_INET6, SOCK_STREAM, IPPROTO_TLS_1_2);
setsockopt(sock, SOL_TLS, TLS_SEC_TAG_LIST, sec_tag_opt, sizeof(sizeof(sec_tag_opt)));
verify = TLS_PEER_VERIFY_REQUIRED;
setsockopt(sock, SOL_TLS, TLS_PEER_VERIFY, &verify, sizeof(verify));
setsockopt(sock, SOL_TLS, TLS_HOSTNAME, "host.name", strlen("host.name"));
// connect to the server
connect(sock, res->ai_addr, sizeof(struct sockaddr_in6));
I have captured a trace of what happens at the modem. I do see the modem receiving the address of the server that I am trying to reach, some back and forth messaging is going on but a connection is not established. I do not see any TLS related messages either, nor do I see any AT messages indicating that the certificate information is sent to the modem at all.
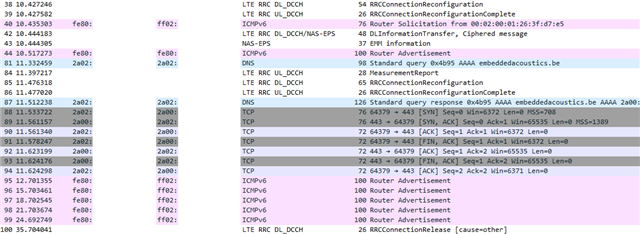
Other than that I don't really know what to make of these logs. Maybe someone here can be of help.


