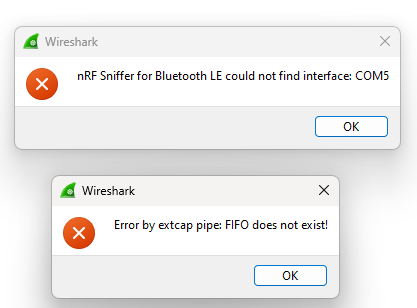
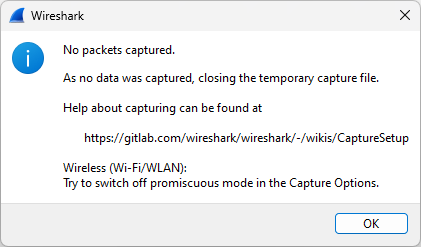
Hello,
I'm using a nRF52 DK to test BLE communication with another microcontroller. What I need to test is the nRF52 pairing with another brand microcontroller, send a data stream and close the connection.
Could you please tell me which example from the Bluetooth samples list I can use for starting?
Thanks for your attention.
Regards,