Hi
I am currently developing a custom dfu in my app in background through LTE communication. I am working with nRF5 SDK 17.0.2, softdevice s132 7.2.0 and nRF52832.
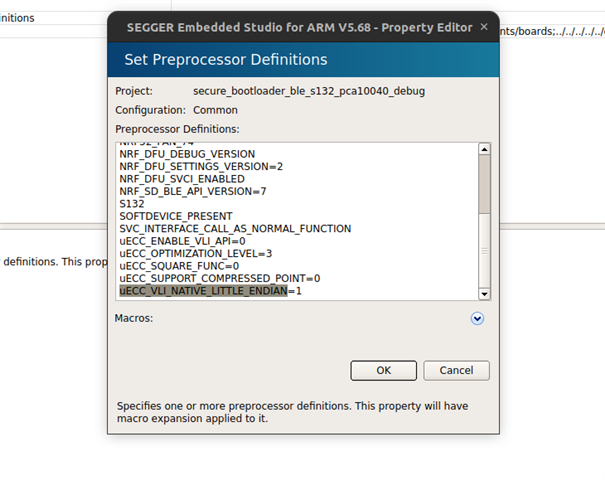
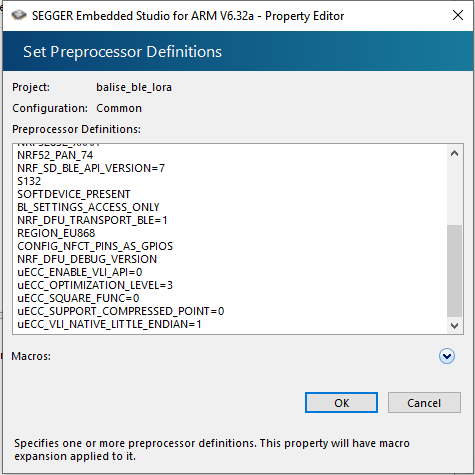
I'm using nrfutil to generate dfu package .zip. The version of nrfutil I'm using seems to be v6 (from command "nrfutil list" because "nrfutil version" is unknown command")
So far I've used nrf_dfu_req_handler module to make dfu requests with the following sequence complying with DFU protocol :
- Call nrf_dfu_req_handler_init() to init module
- MTU GET request
- CREATE OBJECT request
- WRITE command for Init Packet
- Compare CRC and EXECUTE request
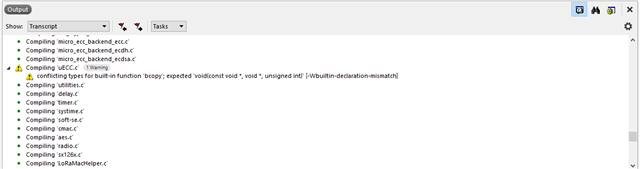
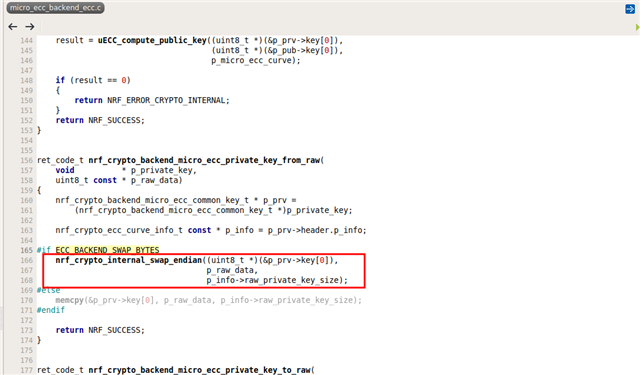
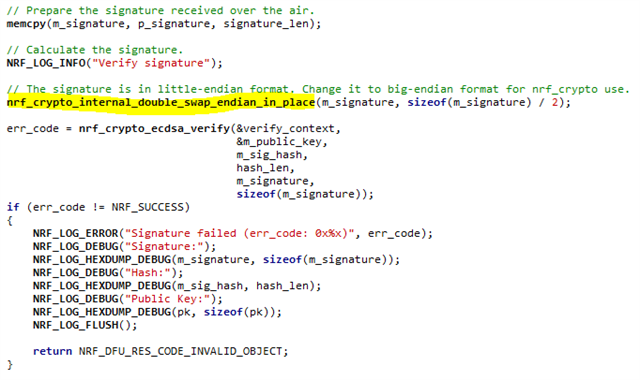
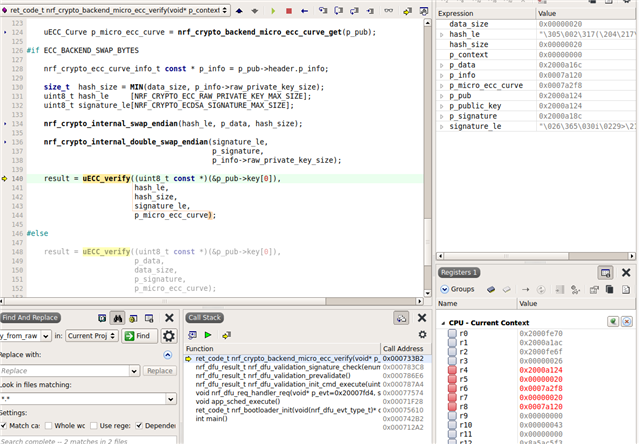
At this point the validation fails with error code 0x8542 (NRF_ERROR_CRYPTO_ECDSA_INVALID_SIGNATURE). See the following logs :
I have displayed the signature of the package .zip I generated with nrfutil by typing :
and it corresponds to the signature in the logs but with first and last halves switched.
How do I solve this issue ?
Also in the logs above there is a line "nrf_dfu_validation: PB: Init packet data len: 65". However the init packet I write with WRITE request is 142 bytes long. The write request response confirms that size (=offset) of 142 bytes. I wonder if this has something to do with my issue above.