Hi! Following my last post, I continue having problems with Zephyr Peripheral NFC Pairing Example on verifying the packets exchanged since as soon as I touch the NFC antenna with my smartphone I cannot see any Security Manager Protocol (SMP) packet exchanged in Wireshark. I needed to visualize these packets to ensure that Pairing Feature Exchange and next pairing steps (key exchange) are occurring as intended (LE Secure Connections OOB pairing).
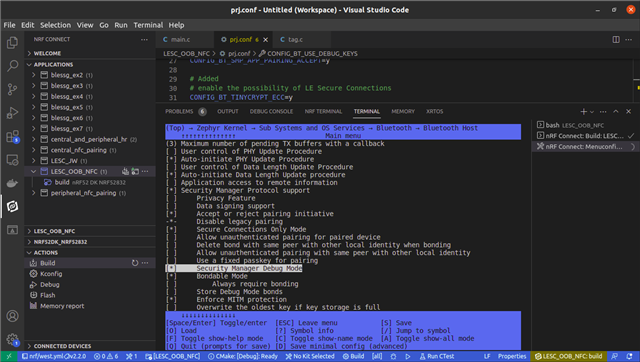
I checked out the Sniffing the pairing procedure of a connection in the nRF Sniffer user guide. Since I am using LE Secure Connections I had to enable Secure Connections Debug Mode on the device. So, for that I added the CONFIG_BT_USE_DEBUG_KEYS=y on the prj.conf. However, after this I continued not to see any Security Manager Protocol (SMP) packet exchanged in Wireshark during the pairing procedure. I also checked out the menuconfig for exploring the available Kconfig options and ensure that the Secure Connections Debug Mode option is enabled.
Thank you for your help!