Hi.
I am using the nRF52810 for Bluetooth SIG certification.
S112 6.0.0
SDK 15.0.0
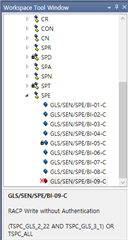
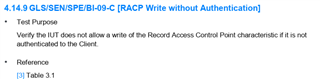
I am testing using ICS of QDID 102861 and 49943, but a failure occurred in the GLS/SEN/SPE/BI-09-C items.
Please check the PTS log below:
Test case : GLS/SEN/SPE/BI-09-C started - Connection setup successfully. - Tester successfully initiated connection. - Paring process is done. Access is granted. - Waiting for encryption change request! - Encryption change event received. - Encryption is successfully done. - LE Security procedures completed successfully. - Discover Primary Service by Service UUID Request completed successfully. - The IUT successfully returned the UUID for Glucose - Discover All Characteristics of Service Request completed successfully. - Discover All Characteristic Descriptors Request completed successfully. - Discover All Characteristic Descriptors Request completed successfully. - Discover All Characteristic Descriptors Request completed successfully. - Connection is disconnected successfully. - Connection setup successfully. - Tester successfully initiated connection. - Discover Primary Service by Service UUID Request completed successfully. - The IUT successfully returned the UUID for Glucose - Discover All Characteristics of Service Request completed successfully. - Discover All Characteristic Descriptors Request completed successfully. - Discover All Characteristic Descriptors Request completed successfully. - Discover All Characteristic Descriptors Request completed successfully. - Connection is using encryption, please disable encryption for this test case. - Connection terminated successfully. -Final Verdict: FAIL GLS/SEN/SPE/BI-09-C finished
A popup appears to disable encryption.
How can I modify the program??
I use static passkey.