Hi,
I am trying to send some information from the application image (e.g. header, TLVs, etc.) through a SPI channel.
The problem is that whenever I try to copy the header information of the application from Flash to a buffer in RAM I always get a fault, and I don't understand why. My pointers are correct, I have tried memcpy, a for loop, direct byte by byte copy, and always get the same result. Are there any restrictions to copy Flash to RAM?
As an example, the code below is just trying to copy the magic value (4 bytes) from the application's header to a buffer in RAM. As mentioned, using memcpy, a for loop, direct copy, will cause a fault. I know my destination buffer is fine, because I can just write a value to it and it works without generating the fault.
Thoughts?
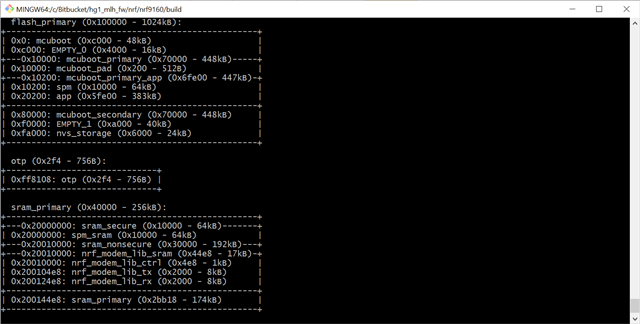
const uint8_t *image_header = (const uint8_t *)0x10000;
uint8_t magic_nr_length = sizeof(uint32_t);
#define OPT 0 // This is to select the example code to copy the magic to the RAM buffer.
#if OPT == 0
memcpy(tx_data.buffer, image_header, magic_nr_length); // This causes a fault.
#elif OPT == 1
for (uint16_t i = 0; i < magic_nr_length; i++) // This causes a fault.
{
tx_data.buffer[i] = image_header[i];
}
#elif OPT == 2 // This causes a fault
tx_data.buffer[0] = image_header[0];
tx_data.buffer[1] = image_header[1];
tx_data.buffer[2] = image_header[2];
tx_data.buffer[3] = image_header[3];
#else
// This does not cause a fault.
tx_data.buffer[0] = 0x96;
tx_data.buffer[1] = 0xf3;
tx_data.buffer[2] = 0xf8;
tx_data.buffer[3] = 0x3d;
#endif
Thanks in advance.