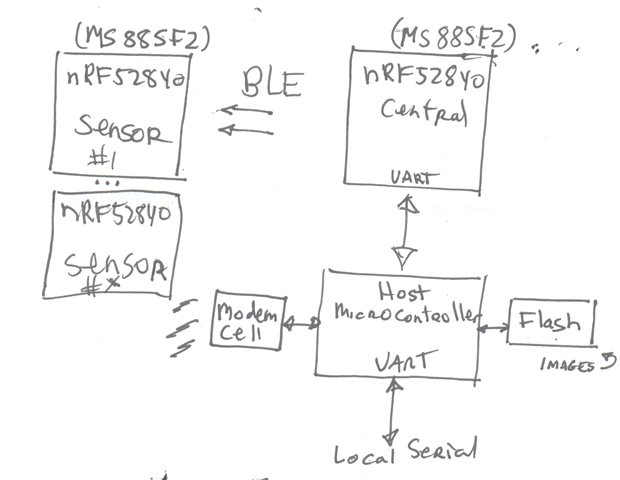
We have nrf52840 S140 BLE Central device that currently connects to TI based sensors. I have implemented code that can upgrade those TI sensors' firmware using the TI BLE protocol.
Now we are developing our own BLE peripheral sensors also based on the nrf52840 but now using the newly supported Zephyr 2.0.0. RF connect stuff. I can update the sensors using the Nordic Android program (unauthenticated for now) and now need to implement upgrading BLE DFU using our central device which connects to a cellular gateway.
I do not want to reinvent the wheel, writing existing code, like I had to do with the TI sensors.
Could you point me to code that allows a Central device to update a peripheral device BLE DFU?
If not where can I look to reinvent another wheel?
Thanks David