Hello,
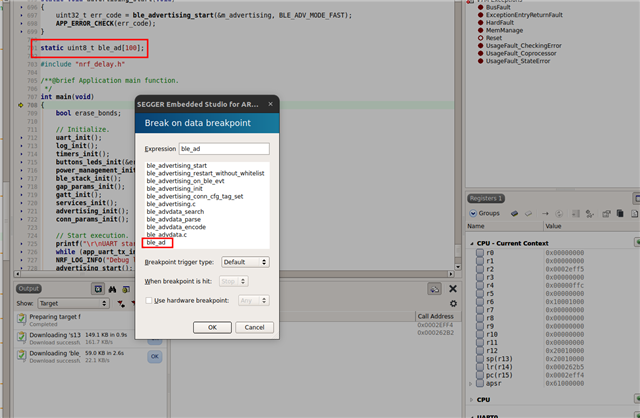
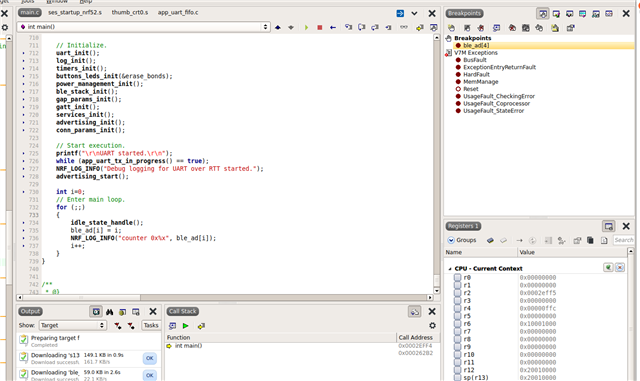
I am trying to set a data breakpoint expression on a global array or global variable but I don't seem to be able to.
Each time I set a data breakpoint I get a '?' next to the breakpoint. See attached picture.
uint8_t ble_ad[HB_BLE_AD_BUFF_SIZE_MAX].
I am using segger Embedded Studio v5.60 and nRF52833 SoC.
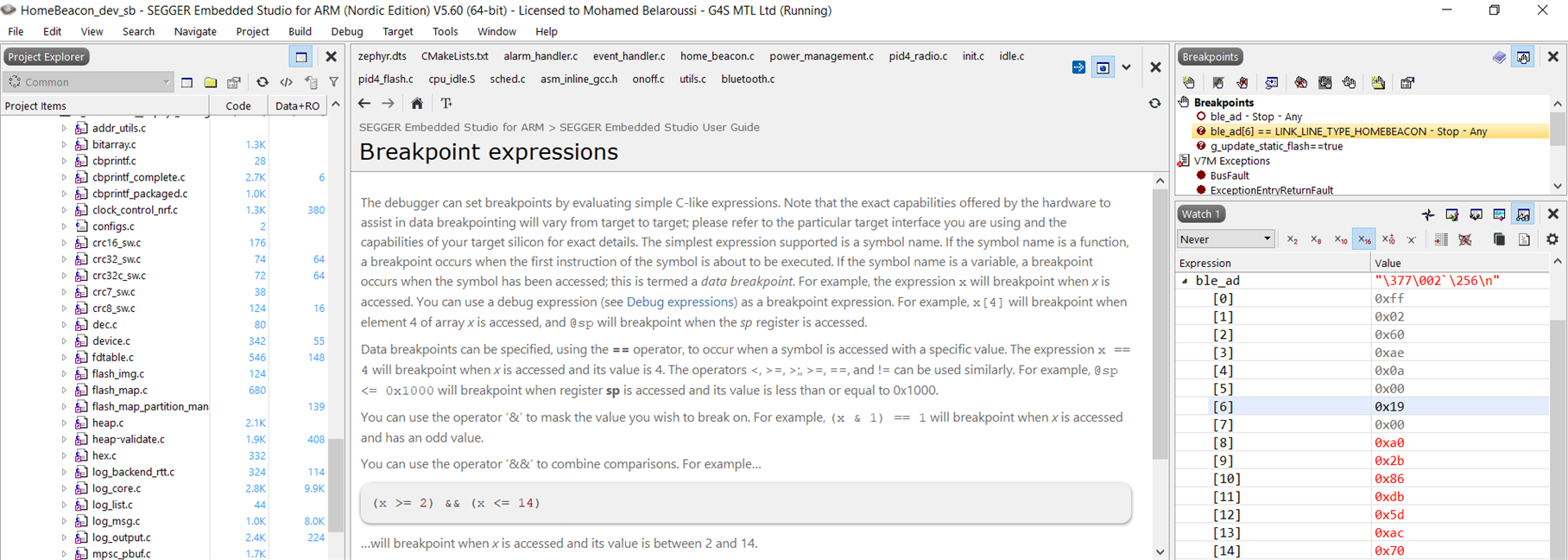
Thank you.
Kind regards
Mohamed